As artificial brains (AI) continues to be able to advance, AI computer code generators have come to be increasingly prevalent in the development of applications. These tools leverage sophisticated algorithms to generate computer code snippets, automate coding tasks, and even build entire apps. While AI computer code generators offer important benefits in words of efficiency and even productivity, they also introduce new protection challenges that must be addressed to ensure code integrity and safeguard against weaknesses. In this post, we’ll explore greatest practices for security testing in AJE code generators to help developers and companies maintain robust, safe code.
1. Be familiar with Risks and Threats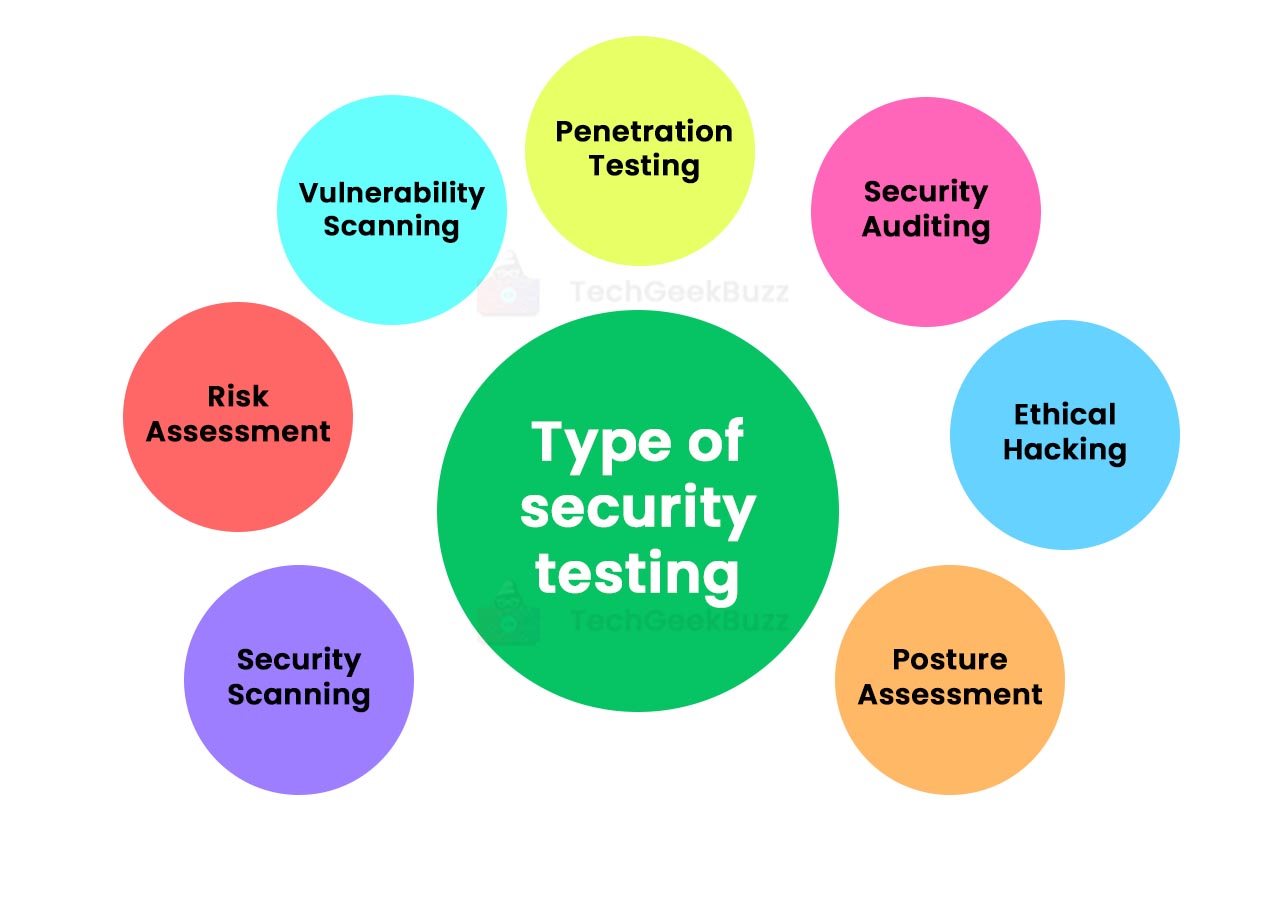
Before diving in to security testing, it’s crucial to understand the potential dangers and threats associated with AI computer code generators. These resources are designed to assist with coding tasks, yet they can unintentionally introduce vulnerabilities otherwise properly monitored. Popular risks include:
Computer code Injection: AI-generated code might be predisposed to code injections attacks, where malicious input is executed within the program.
Logic Flaws: The particular AI may create code with reasonable errors or unintended behaviors that can cause security removes.
Dependency Vulnerabilities: Developed code may depend on external your local library or dependencies with known vulnerabilities.
Data Exposure: AI-generated program code might inadvertently uncover sensitive data when proper data managing practices are certainly not used.
2. Implement Safe Coding Practices
The foundation of safe software development is based on adhering to protected coding practices. When using AI program code generators, it’s necessary to apply these practices to the particular generated code:
Type Validation: Ensure that all user advices are validated and even sanitized to stop injections attacks. AI-generated code should include solid input validation mechanisms.
Error Handling: Appropriate error handling in addition to logging should end up being implemented to steer clear of disclosing sensitive information in error emails.
Authentication and Documentation: Ensure that typically the generated code contains strong authentication in addition to authorization mechanisms to manage access to hypersensitive functionalities and information.
Data Encryption: Employ encryption for information at rest and within transit to guard very sensitive information from not authorized access.
3. Conduct Thorough Code Evaluations
Even with protected coding practices in position, it’s essential in order to conduct thorough signal reviews of AI-generated code. Manual computer code reviews help determine potential vulnerabilities and even logic flaws that the AI may overlook. Below are a few finest practices for signal reviews:
Peer Opinions: Have multiple designers review the created code to get potential issues coming from different perspectives.
Automated Code Analysis: Make use of static code evaluation tools to find security vulnerabilities and coding standards violations in the generated code.
Security-focused Opinions: Incorporate security specialists in the review procedure to target specifically on security aspects of the code.
some. Perform Security Screening
Security testing is usually a crucial help ensuring code honesty. For AI-generated code, consider the pursuing sorts of security assessment:
Static Analysis: Make use of static analysis equipment to analyze the signal without executing it. They can discover common vulnerabilities, this kind of as buffer overflows and injection imperfections.
Dynamic Analysis: Execute dynamic analysis by simply running the program code in a handled environment to determine runtime vulnerabilities and security issues.
Transmission Testing: Conduct transmission testing to reproduce real-world attacks plus assess the code’s resilience against several attack vectors.
Felt Testing: Use felt testing to provide unexpected or unique inputs to the particular code and identify potential crashes or security vulnerabilities.
your five. Monitor and Update Dependencies
AI-generated code frequently relies on outside libraries and dependencies. These dependencies can introduce vulnerabilities or even properly managed. Implement the following methods in order that the security of your dependencies:
Habbit Management: Use habbit management tools in order to keep track associated with all external your local library and their versions.
Regular Updates: On a regular basis update dependencies to their latest versions to benefit from security areas and improvements.
Vulnerability Scanning: Use tools to scan dependencies for known weaknesses and address any kind of issues promptly.
6. Implement Continuous Integration and Continuous Deployment (CI/CD)
Integrating security testing into the CI/CD pipeline will help identify vulnerabilities early on in the enhancement process. Here’s how to incorporate security in to CI/CD:
Automated Tests: Include automated protection testing in the CI/CD pipeline to be able to catch issues while code is incorporated and deployed.
Security Gates: Set upward security gates to be able to prevent code along with critical vulnerabilities coming from being deployed to be able to production.
Continuous Supervising: Implement continuous supervising to detect plus address any safety issues that arise after deployment.
look at here now . Educate and Teach Programmers
Developers participate in an important role within ensuring code ethics. Providing training in addition to education on safeguarded coding practices plus security testing can easily significantly enhance typically the overall security good posture. Consider the subsequent approaches:
Regular Education: Offer regular workout sessions on secure code practices and rising security threats.
Guidelines Guidelines: Develop and even distribute guidelines in addition to best practices with regard to secure coding and even security testing.
Understanding Sharing: Encourage information sharing and effort among developers in order to stay informed about the latest safety measures trends and strategies.
8. Establish the Security Policy
Possessing a comprehensive safety policy helps formalize security practices and guidelines for AJE code generators. Crucial elements of the security policy consist of:
Code Review Procedures: Define procedures with regard to code reviews, which include roles, responsibilities, in addition to review criteria.
Assessment Protocols: Establish protocols for security screening, such as the types associated with tests being executed and their consistency.
Incident Response: Create an incident response plan to tackle and mitigate safety measures breaches or weaknesses that are discovered.
Conclusion
Ensuring code ethics in AI code generators requires some sort of multi-faceted approach that combines secure coding practices, thorough signal reviews, robust protection testing, dependency managing, and continuous checking. By following these types of best practices, programmers and organizations can mitigate potential dangers, identify vulnerabilities earlier, as well as the protection and integrity involving their AI-generated program code. As AI technological innovation continues to evolve, staying vigilant in addition to proactive in safety testing will
become necessary for safeguarding applications and protecting against emerging threats.
Using these practices not necessarily only enhances the particular security of AI-generated code but likewise fosters a traditions of security recognition within development groups. As AI tools become more sophisticated, ongoing vigilance in addition to adaptation to brand new security challenges will probably be crucial in sustaining the integrity in addition to safety of computer software systems.